
Harden Linux with OpenSCAP
OpenSCAP is a tool to automate hardening of Linux servers and workstations. The openscap scanner oscap supports multiple functions including scanning, validation, and remediation. The SCAP Security Guide (SSG) provides ready-made policy definitions for common distributions, and includes remediation content in formats such as Bash scripts or Ansible playbooks to perform configuration changes.
For RHEL-like distros, you can use kickstart to harden the system at installation. Ubuntu claims to support kickstart as well, but I have not tested it.
I’ve found Red Hat support has been generally very good (and Alma/Oracle Linux, by extension). Ubuntu support is also very good, though it generally lags behind RHEL.
Make sure to check the latest release to ensure your distro is supported. As of this writing, the latest SSG version was 0.1.77 and included support for these distributions
tim@lappy scap-security-guide-0.1.77 % ls
ansible ssg-cs10-ds.xml ssg-rhcos4-ds.xml
bash ssg-cs9-ds.xml ssg-rhel10-ds.xml
Contributors.md ssg-debian11-ds.xml ssg-rhel8-ds.xml
guides ssg-debian12-ds.xml ssg-rhel9-ds.xml
kickstart ssg-eks-ds.xml ssg-rhv4-ds.xml
LICENSE ssg-fedora-ds.xml ssg-sle12-ds.xml
manifests ssg-firefox-ds.xml ssg-sle15-ds.xml
README.md ssg-kylinserver10-ds.xml ssg-slmicro5-ds.xml
ssg-al2023-ds.xml ssg-ocp4-ds.xml ssg-tencentos4-ds.xml
ssg-alinux2-ds.xml ssg-ol10-ds.xml ssg-ubuntu1604-ds.xml
ssg-alinux3-ds.xml ssg-ol7-ds.xml ssg-ubuntu1804-ds.xml
ssg-almalinux9-ds.xml ssg-ol8-ds.xml ssg-ubuntu2004-ds.xml
ssg-anolis23-ds.xml ssg-ol9-ds.xml ssg-ubuntu2204-ds.xml
ssg-anolis8-ds.xml ssg-openembedded-ds.xml ssg-ubuntu2404-ds.xml
ssg-centos8-ds.xml ssg-openeuler2203-ds.xml tables
ssg-chromium-ds.xml ssg-opensuse-ds.xmlInstallation
The following were tested in Alma Linux 9 and Ubuntu 22.04 LTS. Find instructions for your specific distro https://www.open-scap.org/download/
For RHEL-like distros
sudo dnf install openscap-scanner scap-security-guide
# Ansible and Kickstart files can be found here
ls /usr/share/scap-security-guide/for Ubuntu 22.04, no packaged SSG datastreams were available, so I had to manually download them
sudo apt update
sudo apt install libopenscap8 unzip
wget https://github.com/ComplianceAsCode/content/releases/download/v0.1.77/scap-security-guide-0.1.77.zip
unzip scap-security-guide-0.1.77.zip
cd scap-security-guide-0.1.77Listing Available Profiles
For Alma, installing via DNF has provided an SSG data stream, which includes all rules, profiles, and remediations.
oscap info /usr/share/xml/scap/ssg/content/ssg-almalinux9-ds.xmlOn Ubuntu, from inside the unzipped directory
oscap info ssg-ubuntu2204-ds.xmlYou’ll get output like this (example in Alma)
Profiles:
...
Title: CIS AlmaLinux OS 9 Benchmark for Level 2 - Server
Id: xccdf_org.ssgproject.content_profile_cis
Title: CIS AlmaLinux OS 9 Benchmark for Level 1 - Server
Id: xccdf_org.ssgproject.content_profile_cis_server_l1
Title: CIS AlmaLinux OS 9 Benchmark for Level 1 - Workstation
Id: xccdf_org.ssgproject.content_profile_cis_workstation_l1
Title: CIS AlmaLinux OS 9 Benchmark for Level 2 - Workstation
Id: xccdf_org.ssgproject.content_profile_cis_workstation_l2
Title: Health Insurance Portability and Accountability Act (HIPAA)
Id: xccdf_org.ssgproject.content_profile_hipaa
...⚠️ Warning: Profiles in DRAFT status are not production-ready.
Title: DRAFT - CIS Red Hat Enterprise Linux 10 Benchmark for Level 2 - Server
Id: xccdf_org.ssgproject.content_profile_cisThere are several profiles to choose from. Some distributions also include profiles for standards such as HIPAA and STIG, for systems that need to meet legal requireents for Healthcare or DoD contractors, respectively. More secure, aggressive profiles are more likely to interfere with the functioning of the system (or even lock you out). A sane baseline choice is CIS server/workstation L1, which aims to provide additional security without interfering with the running system.
Evaluating
Run baseline server security profile (CIS server L1) scan
For Alma Linux
sudo oscap xccdf eval \
--fetch-remote-resources \
--profile xccdf_org.ssgproject.content_profile_cis_server_l1 \
--results-arf alma9-scan-results-arf.xml \
--report alma9-scan-results.html \
/usr/share/xml/scap/ssg/content/ssg-almalinux9-ds.xmlFor Ubuntu
oscap xccdf eval \
--fetch-remote-resources \
--profile xccdf_org.ssgproject.content_profile_cis_level1_server \
--results ubuntu2204-scan-results-arf.xml \
--report ubuntu2204-scan-results.html \
ssg-ubuntu2204-ds.xmlThis will generate a machine readable XML file, as well as a human readable HTML file. You can find an example scan result here (done after remediation).
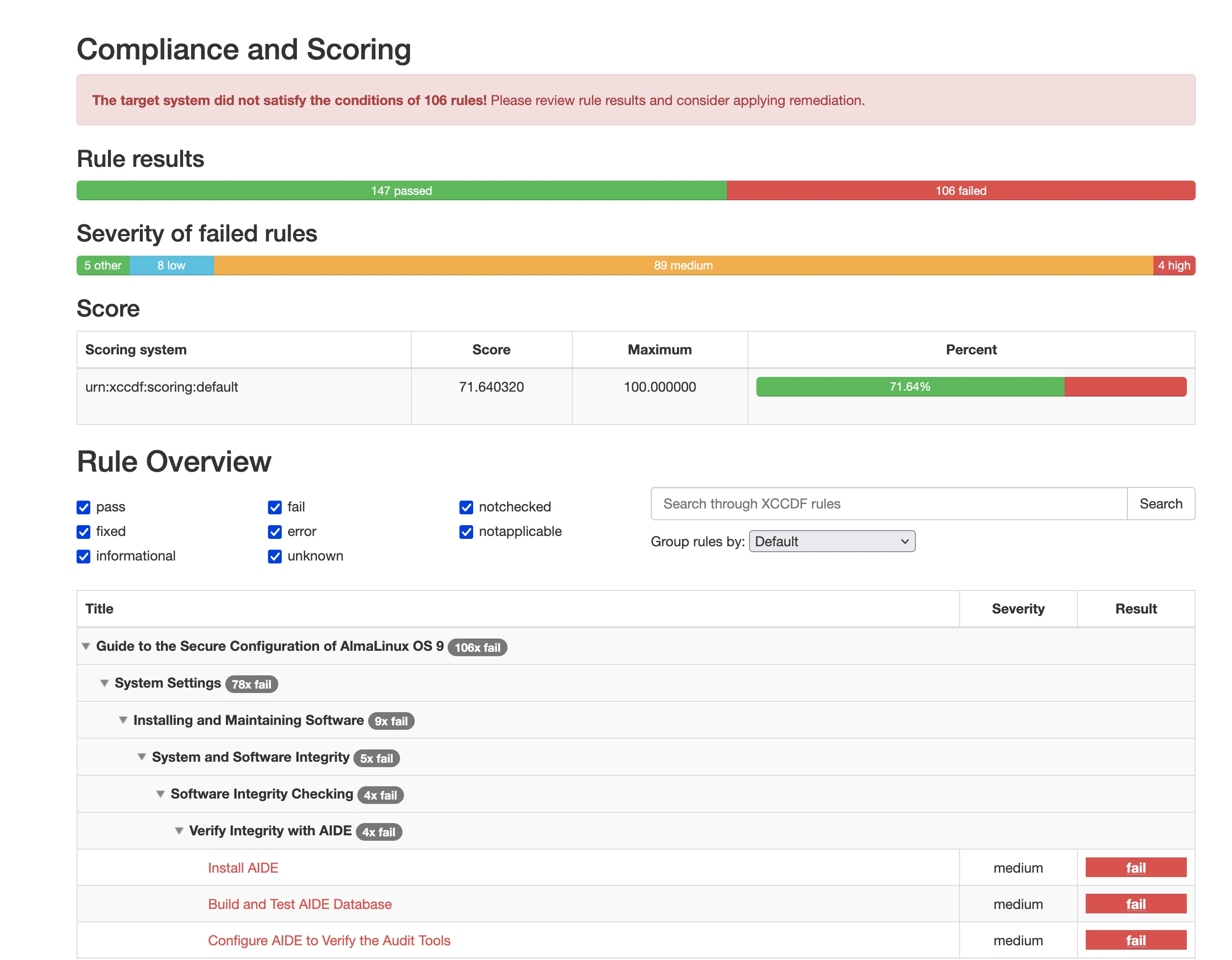
Remediating
To remediate, run the following
⚠️ Warning: You may get locked out of SSH, make sure to test SSH before rebooting if accessing remotely.
In Alma
sudo oscap xccdf eval \
--profile xccdf_org.ssgproject.content_profile_cis_server_l1 \
--results-arf alma9-scan-results-arf.xml \
--remediate \
/usr/share/xml/scap/ssg/content/ssg-almalinux9-ds.xmlIn Ubuntu
oscap xccdf eval \
--profile xccdf_org.ssgproject.content_profile_cis_level1_server \
--results ubuntu2204-scan-results-arf.xml \
--remediate \
ssg-ubuntu2204-ds.xmlSome tasks will require manual intervention, for example configuring the bootloader, creating disk partitions, etc.
Title Ensure the Default Umask is Set Correctly in /etc/profile
Rule xccdf_org.ssgproject.content_rule_accounts_umask_etc_profile
Result fixed
Title Set Boot Loader Password in grub2
Rule xccdf_org.ssgproject.content_rule_grub2_password
Result fail
Title Ensure System Log Files Have Correct Permissions
Rule xccdf_org.ssgproject.content_rule_rsyslog_files_permissions
Result fixed
Title Install systemd-journal-remote Package
Rule xccdf_org.ssgproject.content_rule_package_systemd-journal-remote_installed
Result fixedReboot the system and perform another evaluation to verify. And just like that, we are 95% compliant. Providing this to your Cyber Security team should get them off your back for a while.
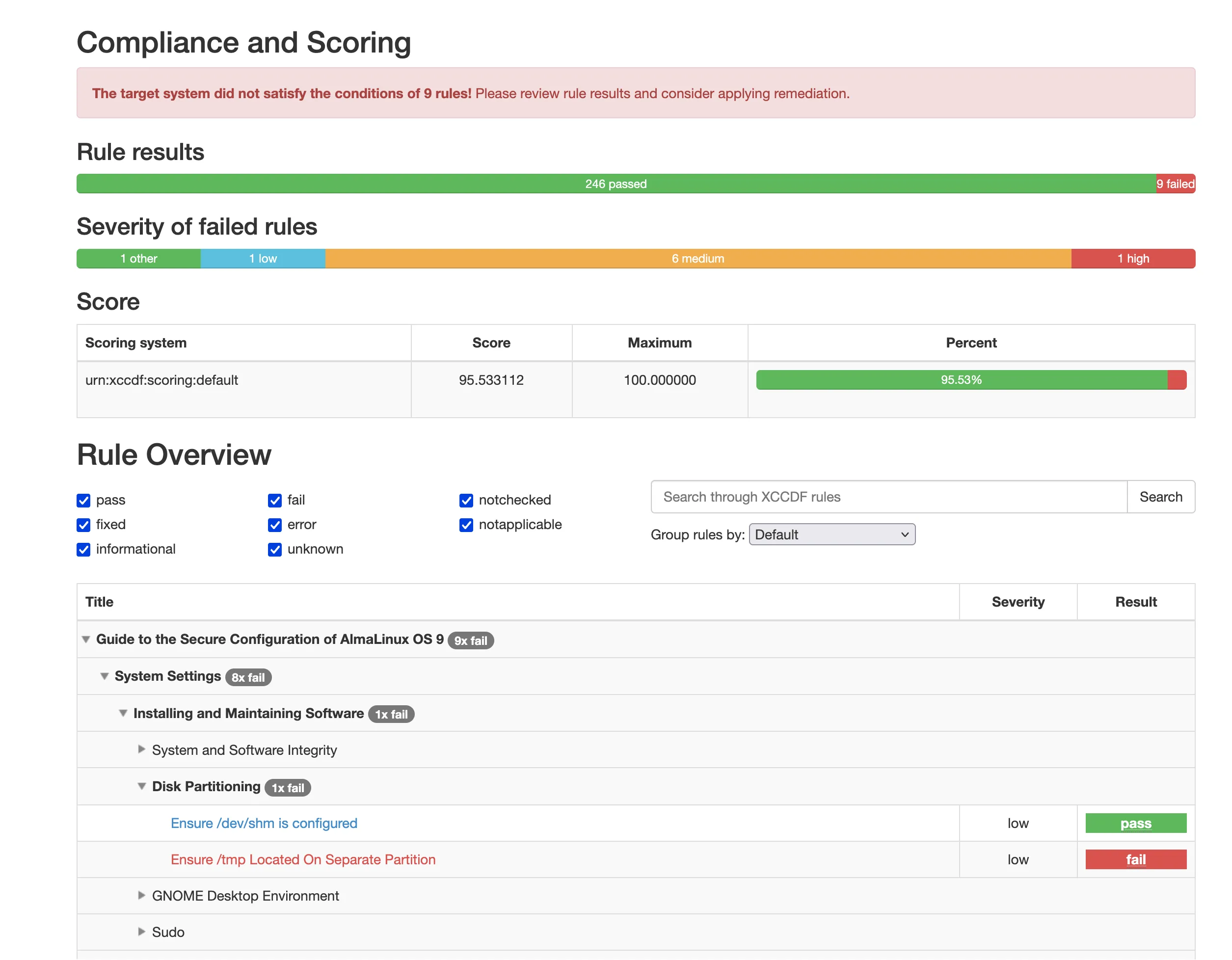
Kickstart Configuration
Using a kickstart file, you can run open scap during the install process. This is especially convenient for on-prem VMs and bare metal servers. I used this SSG provided RHEL kickstart file for Alma (I figure they are similar enough).
These are the lines that run the SCAP configuration
%addon com_redhat_oscap
content-type = scap-security-guide
profile = xccdf_org.ssgproject.content_profile_cis_server_l1
%endI had to make the following changes to the kickstart file for the installation file to succeed in Virtual Box, as XFS filesystem was not supported for the EFI bootloader
# Create primary system partitions (required for installs)
part /boot --fstype=ext4 --size=512
part /boot/efi --fstype=efi --size=512
part pv.01 --grow --size=1Then, make sure to create your own hashed password. You can do this using openssl
tim@lappy Downloads % openssl passwd -6
Password:
Verifying - Password:
$6$co3m5fTPwa7RJXzC$omUul3W1yyRZQ5SyR5/qm/qn8OC8oFwJ6RElpRrDW9F3ULUXYiOtpmt99D7YfcmPKpxhMn4O2qLtuNlqWgk9O0And replace the hashed password in the following line
user --name=admin --groups=wheel --password=$6$co3m5fTPwa7RJXzC$omUul3W1yyRZQ5SyR5/qm/qn8OC8oFwJ6RElpRrDW9F3ULUXYiOtpmt99D7YfcmPKpxhMn4O2qLtuNlqWgk9O0 --iscryptedBoot the ISO
press e to edit Linux boot parameters and append the following kernel parameter inst.ks=nfs://<NFS_SERVER_IP>:/path/to/ssg-rhel9-cis_server_l1-ks.cfg
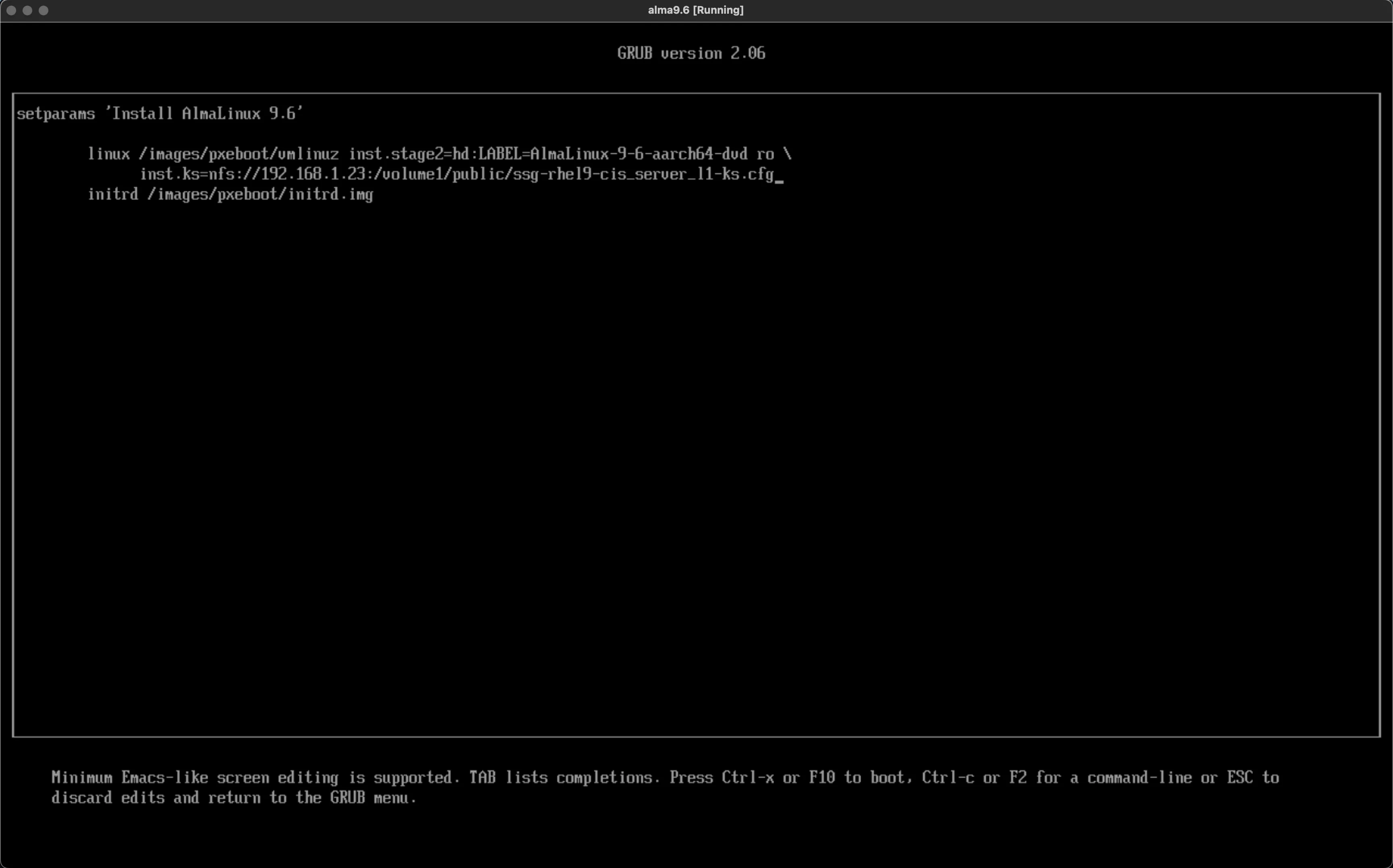
Press CTRL+x to boot. Watch the kickstart and kick back.